Security
Print security is an important subset of an organization’s overall IT security strategy. In fact, printing equipment is really no different than any other endpoint on the customer’s network.
These assets should be managed with the same care and due diligence as other IT technologies to comply with the organization’s overall information security policy. However, some organizations do not view print security as high a priority as warranted. Print security is sometimes mistakenly relegated to secondary status versus other IT categories, particularly as companies seek to be less dependent on paper-based processes. However, it is shortsighted to think of printers and MFPs as just printing assets. Instead, the evolution of this IT category is shifting to a greater emphasis on both paper and digital business processes. This change serves as an indicator that these printing devices will play a critical role in an organization’s overall business processing requirements, regardless of the format in which the content is used. IDC believes that “an unsecured print environment equals an unsecured IT environment.” As such, security of the print environment should be considered during all phases of an MPS engagement.
At the end of 2015, IDC conducted a survey of large organizations in the U.S. and Western Europe that had carried out successful MPS initiatives. Respondents had been engaged with their MPS provider for a minimum of three years. We asked respondents what factors contributed to the success of the MPS engagement at each phase of the engagement. The number one factor for success during the assessment phase of the engagement was that the vendor considered document security requirements. (See Assessment.) A key success factor during day-to-day management of the engagement was that the vendor maintained the security of information and documents (see Manage.)
We asked respondent about the services provided by their MPS vendors to ensure information security. The most common services were authentication for MFPs (57% or respondents), approved configuration sets for devices (54%) and established policies for scanning, email and fax capabilities (47%). 45% of respondents indicated that their vendor continuously monitored for security events.
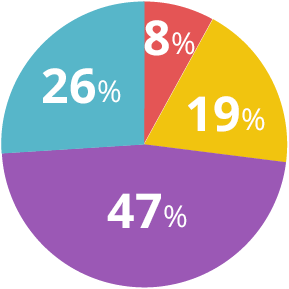
Respondents considered these efforts a success, with 73% indicating that they were “successful” or “very successful” and another 19% saying “somewhat successful.”
Not successful
Somewhat successful
Successful
Very successful